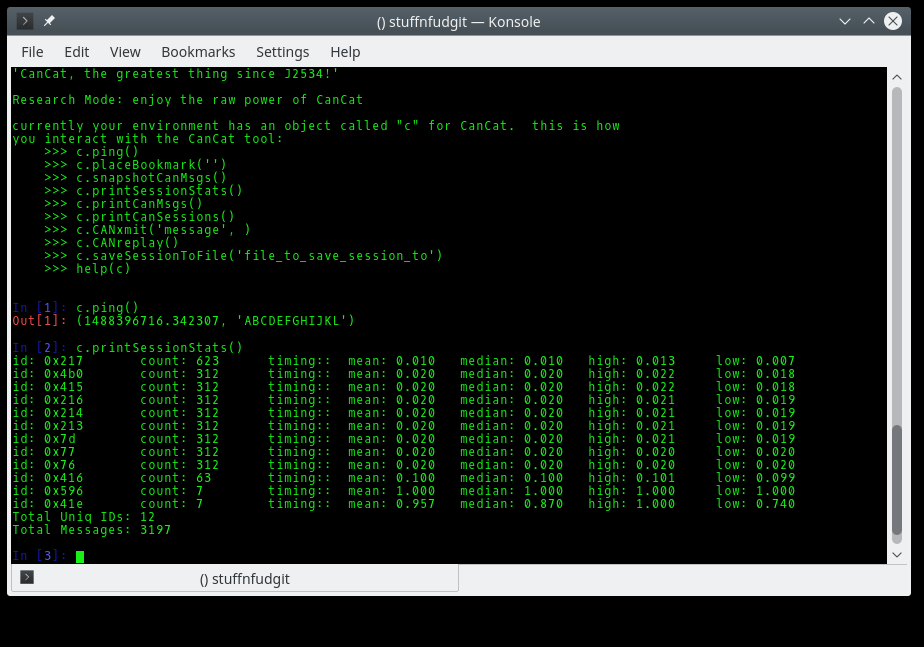
 We asked Tim Brom, a Security Researcher with Grimm, to tell us a little about the state of car hacking and how he plans to use M2 in his research. He writes: As a child, I always looked forward to my parents’ household appliances breaking (sorry Mom and Dad). I knew that once they were broken, I would be allowed to take them apart to see how they worked (so long as I promised not to plug them in…). These early childhood forays into toaster pentesting required little more than a screwdriver and a pair of pliers. There are two things that have changed since then: 1. I break my own appliances now, and 2. There’s a computer in nearly everything. There were no PCBs in the coffee makers of 1992, now they run Linux. The venerable automobile has not escaped this trend. From electronic fuel injection in the 70s to today’s highly connected rolling entertainment centers and on to tomorrow’s autonomous vehicles, auto manufacturers and suppliers are fully committed to technology in the vehicle. A set of wrenches is now less valuable to a weekend car tinkerer than being able to interface with, monitor, modify and control the various Electronic Control Units (ECUs) in a modern automobile. For security researchers, automotive security is a rapidly growing field that desperately needs more people doing high-quality work. There have been a plethora of communication networks used to interconnect various modules in a vehicle. Modern vehicles have largely standardized on CAN (mandated since 2008), LIN and SWCAN. Other (generally older) protocols include J1850 in various forms, ISO9141 and KWP2000. It even has a half-dozen 12V I/O lines that can sink or source up to an amp of current. Unlike most CAN tools the Macchina M2 supports all of these standards, so even if you have an older vehicle the M2 will likely be able to communicate with the ECUs in your car. The M2 can do all of that at a small fraction of the cost of many similar tools. However, the M2 is only one half of the tool. Just as a socket doesn’t do much without a ratchet, the M2 just provides an interface between your computer and the communication network on your car. It requires a software component to allow interactions with the ECUs on that communications network. Some of my colleagues at Grimm and I have been working on software called CanCat that runs on a few platforms, including the M2. CanCat has two pieces, an Arduino sketch (firmware) that runs on the M2 itself and a python module that runs on the computer and allows you to see and control what’s on the CAN bus. CanCat is under active development. It currently supports sniffing raw frames off the CAN bus, sending your own frames, recording and replaying CAN sessions and bookmarks so you can mark exactly when an event took place. CanCat has support for IsoTP (a layer 3 protocol for CAN) and Unified Diagnostic Services (UDS) as well, including functionality to do a brute-force read of all possible Data Identifiers (DID) to see which are valid. Unlocking security access for a few different OEMs is also in the works. Since all of the raw CAN frames are available from within python, writing your own scripts or interacting directly with the M2 with iPython (highly recommended) allows you to use the full power of Python in your analysis. Another useful feature that CanCat has is what we call Can-In-The-Middle mode. One difficulty with reverse engineering CAN is that every message is broadcast and there is no source information, so the information in a CAN frame itself is not sufficient to determine which ECU actually sent the CAN frame. With CAN-In-The-Middle you can electrically isolate one ECU from the rest of the vehicle using the two available CAN ports on the M2 and have the M2 operate in a bridging mode where it forwards the CAN traffic, while simultaneously sending the CAN frames back to Python on the computer. Frames are tagged with which “side” of the connection they came from and you can quickly determine which CAN packets were actually being sent by the isolated ECU. A mode where you can selectively block or modify messages as they pass through the M2 is also planned. The M2 feature that I am most excited about, however, is the wireless connectivity options. Running USB cables out from under the hood of your car and making sure to keep them out of the way so that they don’t get in the way of operating the vehicle safely can be a pain. By using the DIGI XBee form factor a number of inexpensive wireless modules can be added to the M2 to suit your specific needs. In my primary role as a security researcher CanCat’s extensibility and the power of being able to quickly script functionality in Python allows me to focus my efforts on finding vulnerabilities, instead of fiddling around trying to get inflexible toolsets to do what I actually want. We’ve recently used it to attain significant goals on safety-critical ECU’s, including code-execution over CAN. The Macchina M2 with its additional interfaces beyond the CAN bus and wireless connectivity options will allow even more flexibility and capability at a price unmatched by other tools. It will have a place in my toolbox, and it should find a place in yours as well. More information about GRIMM can be found on their site here here
We asked Tim Brom, a Security Researcher with Grimm, to tell us a little about the state of car hacking and how he plans to use M2 in his research. He writes: As a child, I always looked forward to my parents’ household appliances breaking (sorry Mom and Dad). I knew that once they were broken, I would be allowed to take them apart to see how they worked (so long as I promised not to plug them in…). These early childhood forays into toaster pentesting required little more than a screwdriver and a pair of pliers. There are two things that have changed since then: 1. I break my own appliances now, and 2. There’s a computer in nearly everything. There were no PCBs in the coffee makers of 1992, now they run Linux. The venerable automobile has not escaped this trend. From electronic fuel injection in the 70s to today’s highly connected rolling entertainment centers and on to tomorrow’s autonomous vehicles, auto manufacturers and suppliers are fully committed to technology in the vehicle. A set of wrenches is now less valuable to a weekend car tinkerer than being able to interface with, monitor, modify and control the various Electronic Control Units (ECUs) in a modern automobile. For security researchers, automotive security is a rapidly growing field that desperately needs more people doing high-quality work. There have been a plethora of communication networks used to interconnect various modules in a vehicle. Modern vehicles have largely standardized on CAN (mandated since 2008), LIN and SWCAN. Other (generally older) protocols include J1850 in various forms, ISO9141 and KWP2000. It even has a half-dozen 12V I/O lines that can sink or source up to an amp of current. Unlike most CAN tools the Macchina M2 supports all of these standards, so even if you have an older vehicle the M2 will likely be able to communicate with the ECUs in your car. The M2 can do all of that at a small fraction of the cost of many similar tools. However, the M2 is only one half of the tool. Just as a socket doesn’t do much without a ratchet, the M2 just provides an interface between your computer and the communication network on your car. It requires a software component to allow interactions with the ECUs on that communications network. Some of my colleagues at Grimm and I have been working on software called CanCat that runs on a few platforms, including the M2. CanCat has two pieces, an Arduino sketch (firmware) that runs on the M2 itself and a python module that runs on the computer and allows you to see and control what’s on the CAN bus. CanCat is under active development. It currently supports sniffing raw frames off the CAN bus, sending your own frames, recording and replaying CAN sessions and bookmarks so you can mark exactly when an event took place. CanCat has support for IsoTP (a layer 3 protocol for CAN) and Unified Diagnostic Services (UDS) as well, including functionality to do a brute-force read of all possible Data Identifiers (DID) to see which are valid. Unlocking security access for a few different OEMs is also in the works. Since all of the raw CAN frames are available from within python, writing your own scripts or interacting directly with the M2 with iPython (highly recommended) allows you to use the full power of Python in your analysis. Another useful feature that CanCat has is what we call Can-In-The-Middle mode. One difficulty with reverse engineering CAN is that every message is broadcast and there is no source information, so the information in a CAN frame itself is not sufficient to determine which ECU actually sent the CAN frame. With CAN-In-The-Middle you can electrically isolate one ECU from the rest of the vehicle using the two available CAN ports on the M2 and have the M2 operate in a bridging mode where it forwards the CAN traffic, while simultaneously sending the CAN frames back to Python on the computer. Frames are tagged with which “side” of the connection they came from and you can quickly determine which CAN packets were actually being sent by the isolated ECU. A mode where you can selectively block or modify messages as they pass through the M2 is also planned. The M2 feature that I am most excited about, however, is the wireless connectivity options. Running USB cables out from under the hood of your car and making sure to keep them out of the way so that they don’t get in the way of operating the vehicle safely can be a pain. By using the DIGI XBee form factor a number of inexpensive wireless modules can be added to the M2 to suit your specific needs. In my primary role as a security researcher CanCat’s extensibility and the power of being able to quickly script functionality in Python allows me to focus my efforts on finding vulnerabilities, instead of fiddling around trying to get inflexible toolsets to do what I actually want. We’ve recently used it to attain significant goals on safety-critical ECU’s, including code-execution over CAN. The Macchina M2 with its additional interfaces beyond the CAN bus and wireless connectivity options will allow even more flexibility and capability at a price unmatched by other tools. It will have a place in my toolbox, and it should find a place in yours as well. More information about GRIMM can be found on their site here here